Overall security strategy
The security strategy of the network video surveillance system needs to include the security measures of the central platform, front-end access equipment, clients, and software and hardware devices of various parts of the network; the most concerned and the most critical core part, that is, the monitoring center platform is the system The central brain. Through careful security design in terms of physical equipment, network deployment and business applications, the security measures taken at all levels of security and at corresponding levels are shown in Figure 1.
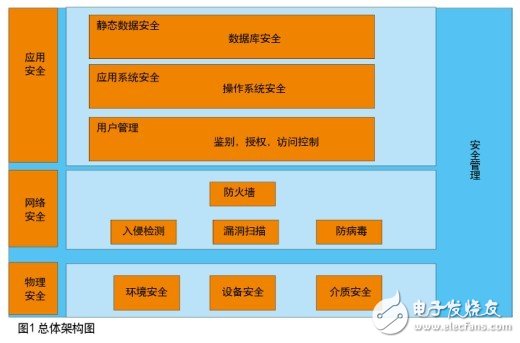
The reliability requirements are as follows:
· Support dual network dual routing mechanism to provide the system with extremely high network security guarantee mechanism;
The database management unit is the core of the system data, and the high-reliability dual-machine hot backup design ensures that the platform works stably and continuously;
· Adopt dynamic load balancing mechanism to make the central management unit, access management unit and business application unit achieve dynamic load balancing to ensure extremely high availability of the system;
· For media forwarding unit, mobile monitoring gateway unit and media storage unit, N + 1 backup design is adopted to ensure that the system will not cause the entire system to crash due to a single device downtime;
· Adopt separate processing of media stream and signaling data stream to ensure the efficient isolation mechanism of the system;
· Key data and media data are stored in a dedicated storage device, using RAID5 or RAID6 and other mechanisms to ensure the safety of data storage.
The system must also take comprehensive security protection measures, involving the system platform, front-end access equipment, clients, and the network that connects the various components. , So that the system has a high degree of security and confidentiality.
Physical equipment security
Physical device security includes various hardware devices in the network video surveillance system, and each component hardware needs to take security measures to achieve the best protection effect.
The equipment on the side of the video surveillance system platform is often placed in the customer's dedicated computer room. The monitoring front-end equipment, especially the field equipment, has a complex and harsh environment, and requires high equipment. For example, the front end of the encoder, camera, etc. is installed in a public place. The explosion-proof camera, encoder and optical communication equipment should be placed in the equipment box and locked. The cable needs to be installed in a casing or concealed. Prevent being destroyed. At the same time, equipment installed outdoors also needs to consider waterproof, high temperature resistance, chassis ventilation, low temperature heating, etc., to ensure that the equipment can work normally in various harsh environments.
1. The server's own security
Security hardening can be considered from two aspects. One is that the monitoring platform generally adopts the Linux operating system with higher security performance. Close processes, applications, ports and services that are not related to the monitoring system business; regularly patch security backdoors, upgrade the system kernel version; standardize login account passwords, restrict remote login reading and writing, and choose a highly secure SSH key method ; Hide and protect important data, such as log records management, etc .; use security tools and regular security checks.
The second is to load anti-virus software and firewall software on each server. The virus definition code should be updated in real time from the server through a dedicated line to prevent the server from being invaded and attacked by viruses.
2. Security of network equipment
The security of network equipment in the video surveillance system includes optical devices, fiber optic transceivers, switches and routers, and other network equipment. Among them, the rational use of the security settings of routers and switches can effectively reduce malicious intrusions by hackers and protect the security of data transmission.
The front-end access end is recommended to use industrial-grade switches. The system platform adopts dual-route dual-switch configuration to establish a master-standby redundancy or load balancing mechanism to enhance safety and reliability. On the other hand, configure security policies for important switch routing devices in the system, such as establishing rules to achieve filtering requirements, port-based access permission, and flow control, strengthening device network management SNMPV3 and SSH secure login, switch log reporting and watchdog Open and firmware image and other safety-related function settings.
3. Firewall security
A firewall refers to an integrated combination of security software and computer hardware equipment. It is mainly composed of four parts: service access rules, verification tools, packet filtering, and application gateways. Set access rules through firewalls, configure different security levels, and allow port services, IP, and protocol data to filter data to reduce system platform server pressure. In general, limited by the performance of the protective wall, the video surveillance media stream does not perform firewall penetration services, and only performs security verification on the signaling and other signaling parts of the system platform to reduce the pressure on the firewall;
4. Double authentication access of front-end equipment
Only legal front-end devices can be registered to the system. The system uses a unique password issuance mechanism to issue random passwords to front-end devices that have passed ID authentication. The system can effectively prevent illegal or fake front-end equipment from accessing the system through the dual authentication mechanism of identity ID and password to ensure the security of the system.
cyber security
The transport layer mechanism is adopted on the bearer network to ensure the security of network transmission. Using private networks to isolate network video surveillance traffic and other traffic, and preferentially selecting a private network (physical private network or VPN network) networking method can ensure the security of network lines, but the corresponding investment in the establishment of a video surveillance private network will increase substantially.
Each egress network connection of monitoring collection can consider two different directions to establish two routes for backup. The equipment that provides services externally to the platform is connected to the DMZ zone of the firewall and connected to external networks (such as metropolitan area networks) through the firewall. In the planning and design of critical network monitoring equipment, network security technical measures such as firewalls, vulnerability scanning, intrusion monitoring, and VPN are used to monitor the operating status of the entire network in real time to ensure safe and reliable operation of the system.
Ftth Drop Cable Assembly,Ftth Drop Cable Assembly Assembly,Ftth Drop Cable Assembly Adapter,Ftth Drop Cable Assembly Access
Huizhou Fibercan Industrial Co.Ltd , https://www.fibercan-network.com